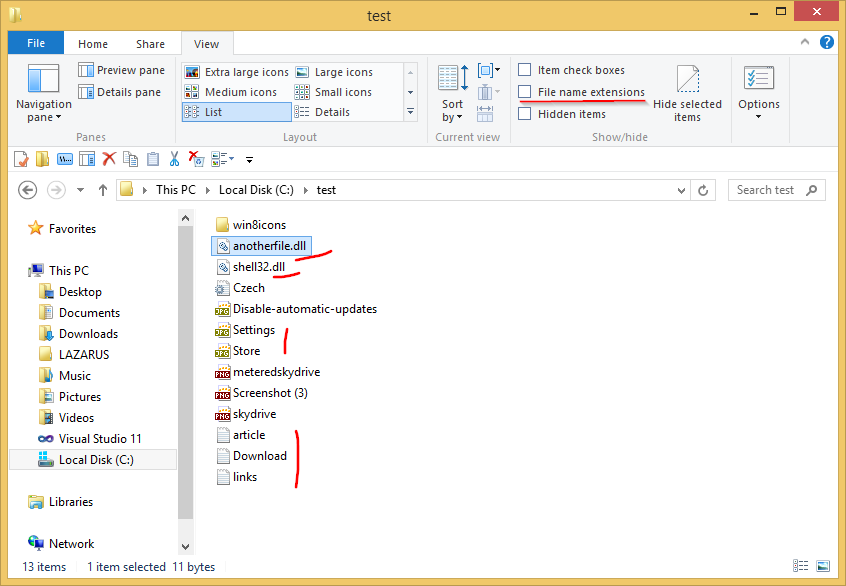
DLL redirection can modify the DLL search order directly to force the program to run the malicious DLL instead of the legitimate one. DLL preloading places an infected DLL with the same name as an ambiguously specified DLL, which will cause the malicious DLL to be searched for first. Make “hello, world” in minutes for any web, mobile, or single-page app. To do this, on your Windows 11/10 computer, right-click on the Start button to open the WinX Menu and click on Command Prompt link. The process known as System or system belongs download api-ms-win-shcore-scaling-l1-1-1_dll to software Cisco Secure Desktop or Dbsqlinfo by Cisco Systems () or Microsoft (). Either way, when you see the program, click on it to start the program.
- Unfortunately with rundll, passing in arguments to functions can get tricky so there are some limitations on which exported functions we can call this way.
- The policy file is primarily used in a business with a large number of computers where the business needs to be protected from rogue or careless users.
- A DLL file contains a set of procedures referenced and executed by a Windows program.
File Viewing (including dynamic link library .dll) is absolutely safe. The purpose of DLL files is to be a collection of functionality (a “library”) that other programs can utilize. This is essentially what rundll32.exe does when it is passed a dll file and function as arguments. This is also why we often see LoadLibrary and GetProcAddress used in malware which implements its own custom loader to load up DLLs which were not specified in the PE Header. The main technical difference that differentiates DLLs from EXE files is the loading process.
Once the modification is enforced, hit Apply to save the changes, then close the Internet Properties window. Once the key has been deleted, close Registry Editor and restart your computer. Its uninstall wizard should open so follow the instructions to uninstall it. Locate your antivirus tool in Control Panel or Settings and click on Uninstall. In Control Panel, select to View as – Category at the top right corner and click on Uninstall a Program under the Programs section. Select files from Computer, Google Drive, Dropbox, URL or by dragging it on the page.
3.1. Tar File Installation
“How to add, modify, or delete registry subkeys and values by using a .reg file”. The registry checker tool backs up the registry, by default, to %Windir%\Sysbckup Scanreg.exe can also run from MS-DOS. Outside security, registry keys cannot be deleted or edited due to other causes. Registry keys containing NUL characters cannot be deleted with standard registry editors and require a special utility for deletion, such as RegDelNull. Data from .REG files can be added/merged with the registry by double-clicking these files or using the /s switch in the command line.
You can download all the necessary DLL files from WikiDll.com for absolutely free. Next, choose a category to view the names of all installed devices. Once you click the button, your device will reboot automatically and start scanning your PC for viruses and malware. If a malicious entity is detected, you will be advised to clean it up or have it quarantined.
The file contains a directory of the individual methods (procedures, routines, etc.) contained within the DLL and the types of data they take and return. As a result, you will see a list of installed programs on your computer, and you can choose the right one. We also recommend checking the box next to “Use this application for all INI files”. It does not represent anything complicated, any user can understand it. There are various directives on the left side of the program. In the central part of the utility, there are codes that can be changed during the work and then saved.
how can i open dll file??
Parameter lists the synchronization objects to isolate from other applications. Parameter can force Windows to load specific DLL files from the virtual file system. Parameter determines whether Windows creates and runs COM objects in the physical environment, rather than the virtual environment, to facilitate application compatibility with ThinApp. Unsafe C# code is code that is able to access memory directly. It is not enabled by default because the compiler can’t verify that it won’t introduce security risks.
RPG MAKER VX ACE RUNTIME PACKAGE VER. 1.00 END USER LICENSE AGREEMENT
The purpose of doing this to analyze files requires an analyst to first have dynamic monitoring tools running and ready to go. I am sure it is loading the file because if i remove the dll file from this folder it is giving no dll file in library path error,so it is loading dll file but not executing the function. If a startup repair fails to debug DLL errors, a clean installation is a good solution if DLL missing or not found errors are based on software. But this way can wipe out everything from your hard drive including the operating system files, hence, please back up the entire disk in advance. Read this post and you will know how to recover these files with MiniTool data recovery software, as well as how to fix this issue by some other solutions. Specifies the type of machine for which the library file should be built.